SAML2 Azure
The SAML2 configuration requires a valid Office 365 subscription, Azure AD Premium P2 is recommended.
Add a new enterprise registration
Portal.azure.com/Azure active directory/ Enterprise applications / New application
Select “non-gallery application”
Name: MFAS Portal (or a name of choice).
Assign users and groups
Assign users or groups (maybe a test group at first)
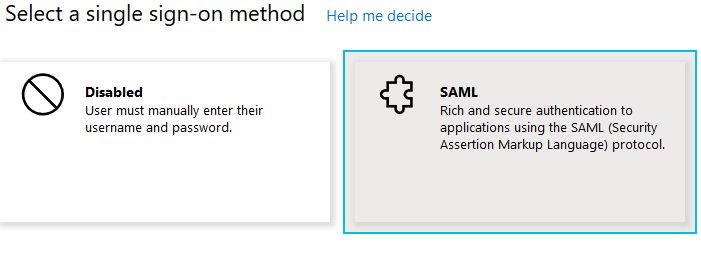
Set up single sign on
Select “SAML”
Download the SSO Gateway metadata
Browse either to:
https://www.mfas.nl/sso/ibm/saml20/<customerid>/samlmetadata
In the above URI’s, the term “<customerid>” must match the Customers unique id and will be provided by the MFAS Portal administrator.
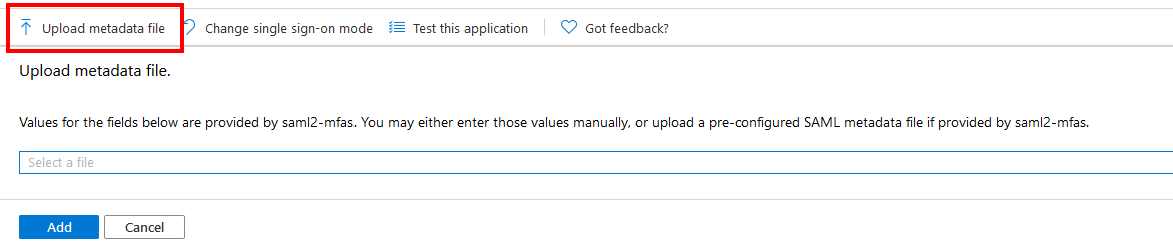
Upload the metadata to Microsoft Azure
Set the basic SAML Configuration
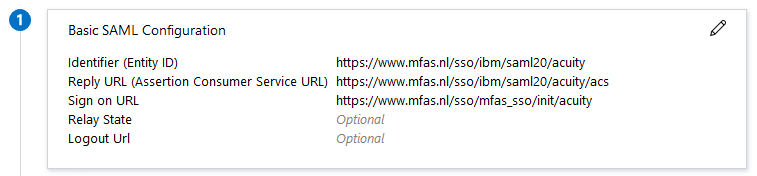
Examples:
Identifier: https://www.mfas.nl/sso/ibm/saml20/acuity
Reply URL (Assertion Consumer Service URL): https://www.mfas.nl/sso/ibm/saml20/acuity/acs
Sign on URL: https://www.mfas.nl/sso/mfas_sso/init/acuity
In the example above, “acuity” is the customerid.
Leave the user attributes & claims as default
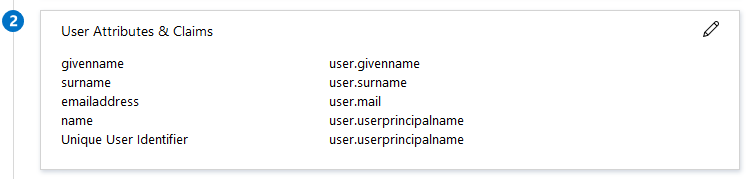
Givenname: user.givenname
Surname: user.surname
Emailaddress: user.mail
Name: user.userprincipalname
Unique User Identifier: user.userprincipalname
Provide the metadata
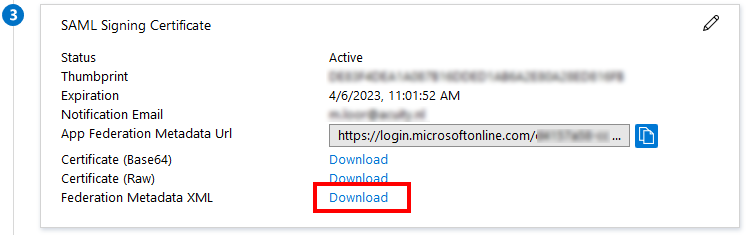
Send the downloaded XML file to the MFAS Portal administrator.
You can also provide the “app federation metadata URL”
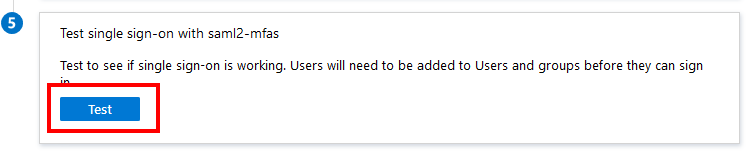
Test the SSO.with a valid user
Note: Before the test can be performed, the MFAS Portal administrator needs to confirm the Federation Metadata XML file has been processed on the server. If the metadata has not been processed, all tests will fail!
Press the test button: